demonstration
Step 1
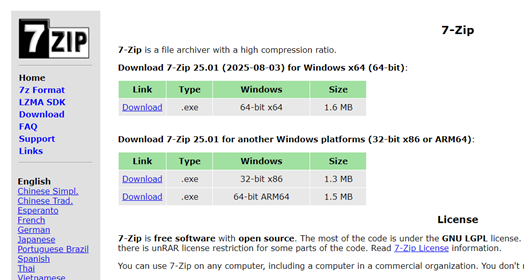
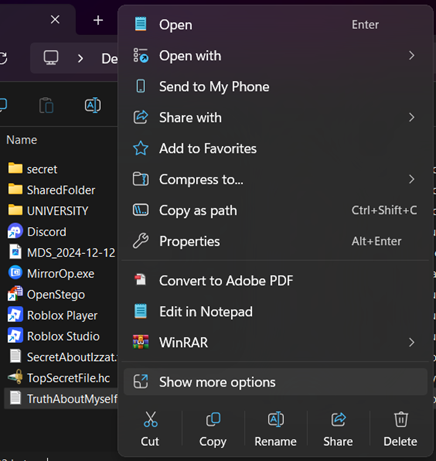
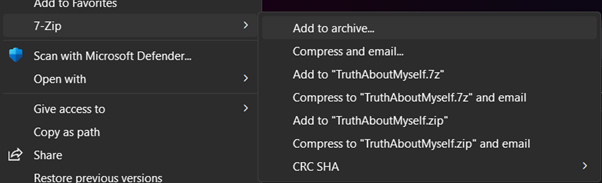
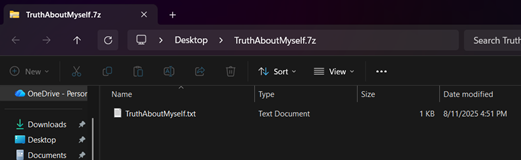
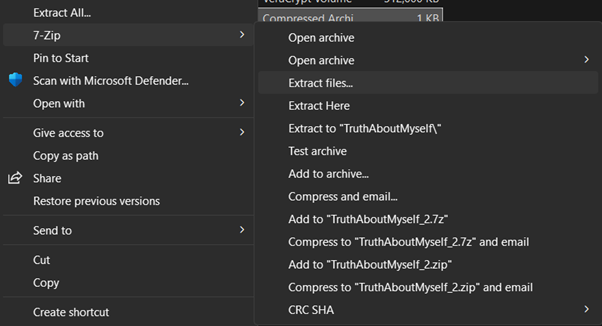
1. Choose the file that you want to protect. Right-click on the file, select Show more options, click 7-Zip, and then select Add to archive.
Step 2
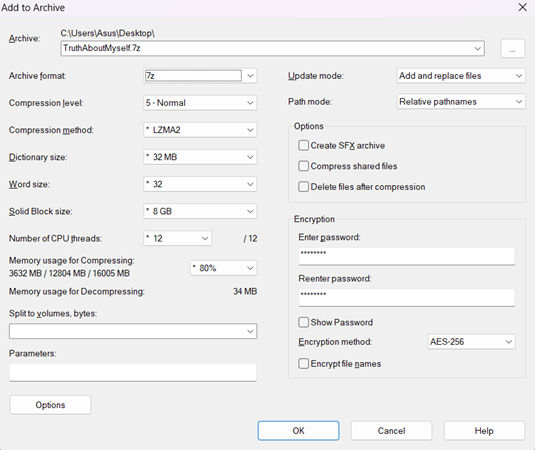
2. A window Add to Archive will appear. Make sure the Archive format is “.7z”. Under Encryption section, enter password and also re-enter the password again. For Encryption method select AES-256. Double check all settings and click OK. The .7z will be created at the path as shown at the top of the window.
Step 3

3. An encrypted archive file with the .7z is created. Original file contents are now protected.
Step 4
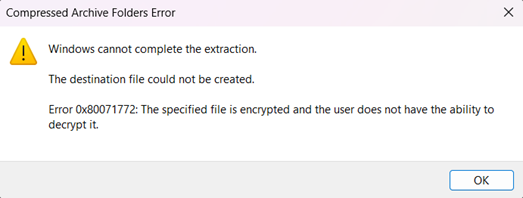
4. To verify whether the encryption process works, try to double click the .7z encrypted file. An alert window will pop up, meaning that when you attempt to open without a password, you cannot access to the encrypted file.
Step 5
5. To decrypt the file, right-click on the .7z file, select Show more options, click 7-Zip, and choose Extract files.
Step 6
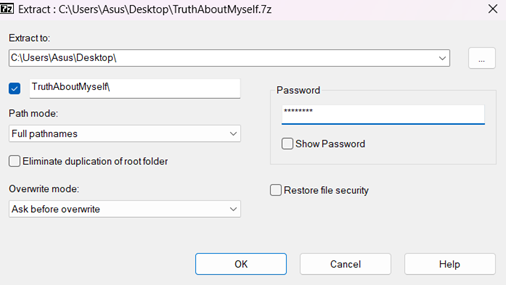
A window will appear asking for a password. Enter the password that was created during the encryption process and click OK.
Step 7
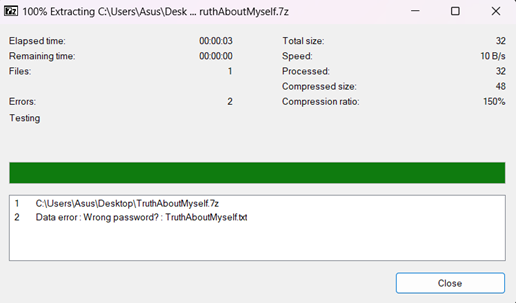
7. If no password or an incorrect password is entered, an error message will appear stating that the password is wrong. This shows that without the correct password, the encrypted file cannot be accessed or extracted.
Step 8
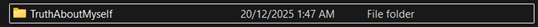
8. After entering the correct password, the file will be successfully extracted. You can now access and open the file, which means the file has been successfully decrypted.